Idea 091 - Honeypot terrarium
This post is part of the 100 project ideas project. #The100DayProject. I am looking for feedback. Comment below or DM me via social media Instagram, Twitter.
One Line Pitch
Visualization of robots as they attack critical infrastructure using Conways Game of Life
Description
Honeypot
I once made a fake BACnet IP device and put it on the public internet (No firewall). It took 3 mins before it was discovered and a robot tried to write to the changeable values (Analog outputs, Binary outputs). The device mimicked an active coal power plant in its object names (dump steam valve, emergency shutdown, etc…) and object lists. 3 mins, and robots tried to destroy a power plant. I did the same thing with Modbus TCP with similar results.
It was an eye opening experience for me, to show how much damage could be done by accidentally exposing your critical infrastructure to the internet. Also how important it is to have protocols that have encryption and authentication as a core aspect of the protocol.
Creating these kinds of fake devices to detect and log unauthorized access or attacks on devices is often called honeypots. You basically bait the robots into attacking you, then ban their accounts or IP address from access to your real devices.
Visualizing IPv4
 The IPv4 address range can be split up and visualized on a grid by using the first two octets of the IP address {One}.{Two}.X.X. Using the example of 104.21.35.195, One=104, Two=21. The last two octets are dropped and ignored.
The IPv4 address range can be split up and visualized on a grid by using the first two octets of the IP address {One}.{Two}.X.X. Using the example of 104.21.35.195, One=104, Two=21. The last two octets are dropped and ignored.
The first octet (104) you use with a fractal pattern to align the address space on a plane that preserves grouping of IP addresses. See Map of The internet by XKCD
The second octet can be split up into a grid. With 1 in the top left corner and 255 in the bottom right hand corner.
This allows us to visualize the IPv4 address range across a grid.
Conway’s Game of Life
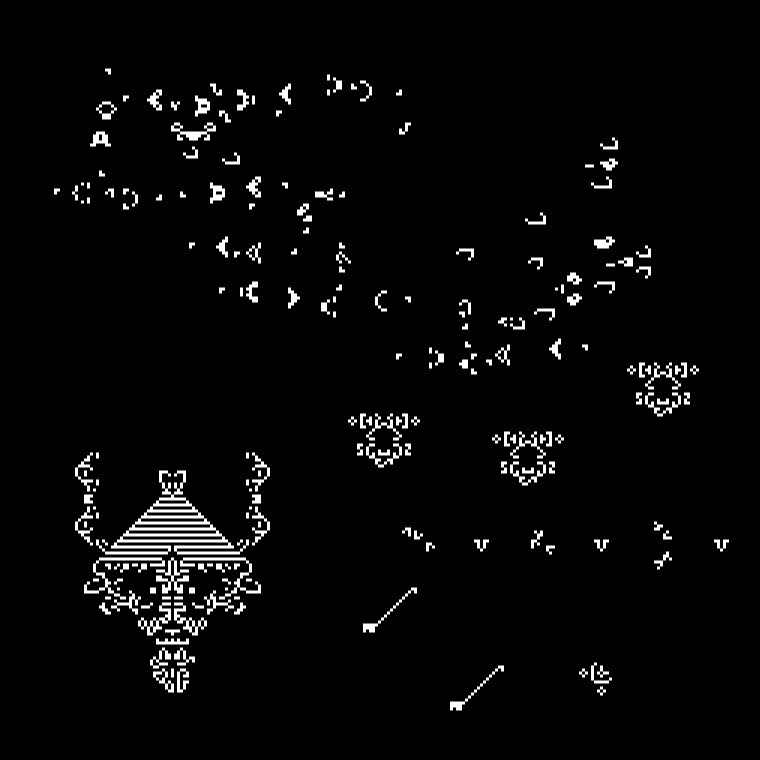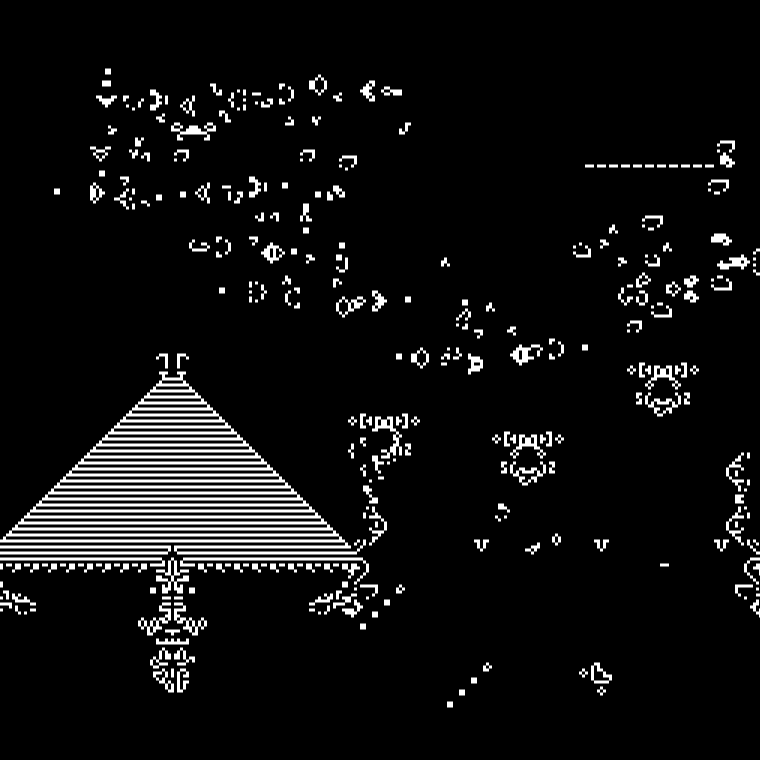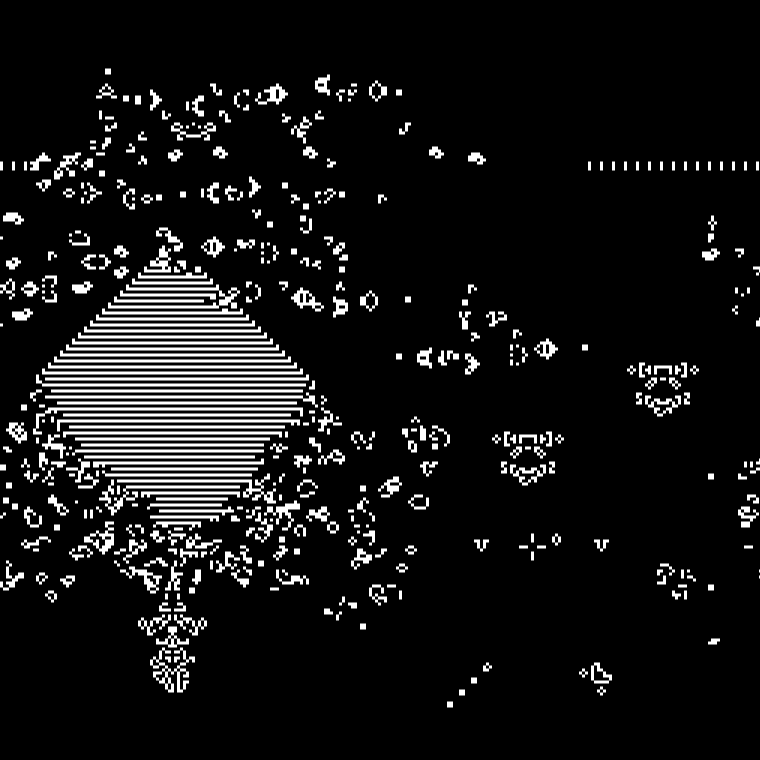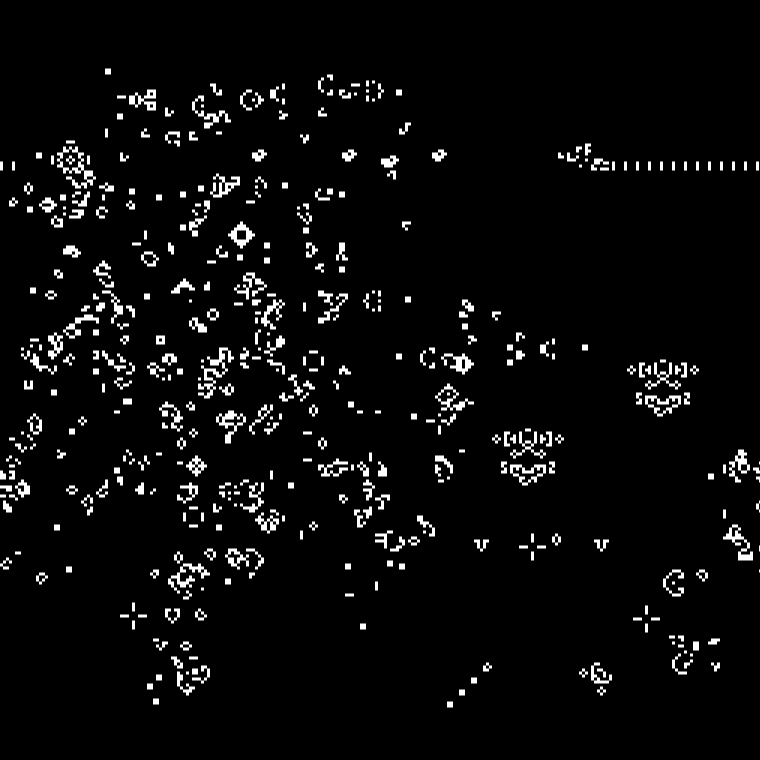 Conway’s Game of Life is a cellular automaton zero player game.
Conway’s Game of Life is a cellular automaton zero player game.
The universe of the Game of Life is an infinite, two-dimensional orthogonal grid of square cells, each of which is in one of two possible states, live or dead (or populated and unpopulated, respectively). Every cell interacts with its eight neighbors, which are the cells that are horizontally, vertically, or diagonally adjacent. At each step in time, the following transitions occur:
- Any live cell with fewer than two live neighbors dies, as if by underpopulation.
- Any live cell with two or three live neighbors lives on to the next generation.
- Any live cell with more than three live neighbors dies, as if by overpopulation.
- Any dead cell with exactly three live neighbors becomes a live cell, as if by reproduction.
These rules, which compare the behavior of the automaton to real life, can be condensed into the following:
- Any live cell with two or three live neighbors survives.
- Any dead cell with three live neighbors becomes a live cell.
- All other live cells die in the next generation. Similarly, all other dead cells stay dead.
Honeypot Terrarium (putting it all together)
Create a series of industrial protocol (BACnet, Modbus, Lonworks, Veeder root, DNP3, SNMP, Danfoss, Siemens, OPC UA, Rockwell, Ethernet/IP, MBus, MQTT, Notifier, OPW) honeypots
Make these honeypots mimic critical infrastructure such as Electricity generation, communication systems, water treatment plants, fire suppression systems, nuclear research labs, hospitals, airports, telecommunication, banking systems, oil and gas extraction, military complexes, manufacturing. The mimic devices that would cause a lot of damage if someone was to randomly change values. Attractive targets.
When these honeypots are attacked, record the IP address and visualize it on the map of IPv4 address.
The visualization could be as simple as a heat map. Increasing the intensity of the region where the attack happened. It would be informative and you see what regions most of the attacks come from. The image wouldn’t be very active as the whole map slowly intensifies.
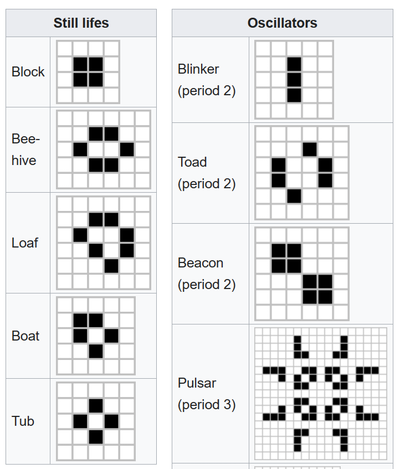 Instead, when an attack happens, create random Conway’s Game of Life creatures in the grid where the attack originated from.
Instead, when an attack happens, create random Conway’s Game of Life creatures in the grid where the attack originated from.
- Still lifes: Block, Bee-hive, Loaf, Boat, Tub
- Oscillators: Blinker, Toad, Beacon, Pulsar
- Spaceships: Glider
If a glider goes off the edge of the grid make it loop to the other side. So it doesn’t disappear from the map.
Add ghosts to the dead cells, where they slowly fade away when they die instead of disappearing entirely.
Only tick the clock/iteration when a new attack happens. The more attacks the faster the animation occurred. This should mean that the screen will always have some alive cells on the screen at any given time
Maybe each attack is colored depending on what industrial protocol that is used for the attack. BACnet=Blue, Modbus=Red, etc…
Prior art
- Map of The internet (#195), and Network (#350) by XKCD.
- Inkplate e-ink screen shows Conway’s Game of Life, seeded from tarpits
Market
Anyone in security, anyone who works in critical infrastructure.

Leave a comment